http://d.pr/B0tw. So it's easy
to land on the idea that they are more or less "out of band" URLs. Similar to
what you get when you share a Dropbox file – a long random string that is
basically unguessable. Except they're not, because of the desire for Droplr to
shorten the URLs to make them copy-paste friendly.
The URLs are unassociated, certainly, but that just means that for a random
file X, there is no direct association to the person who posted it.
Unless the content of X implies something about the user. Or,
X gives something away that the user would rather it didn't. Either way.
A friend sent me a link via Skype, and after clicking it, the implication
of the short d.pr domain finally dawned on me. If the intention is
to provide short URLs, it's implied that you will start at a small index and
grow outward. Meaning it's easy to discover links that result in some kind of
payload. To create an "out of band" URL you must use a sequence large and random
enough so that guessing it is improbable.
(This has been true since tinyURL made URL
shortening a thing. However, that service didn't also combine the ability to
upload content at the same time, which is the bad mix, in my opinion.)
So I deleted one character from the URL my friend sent me, and sure enough I got
someone else's drop.
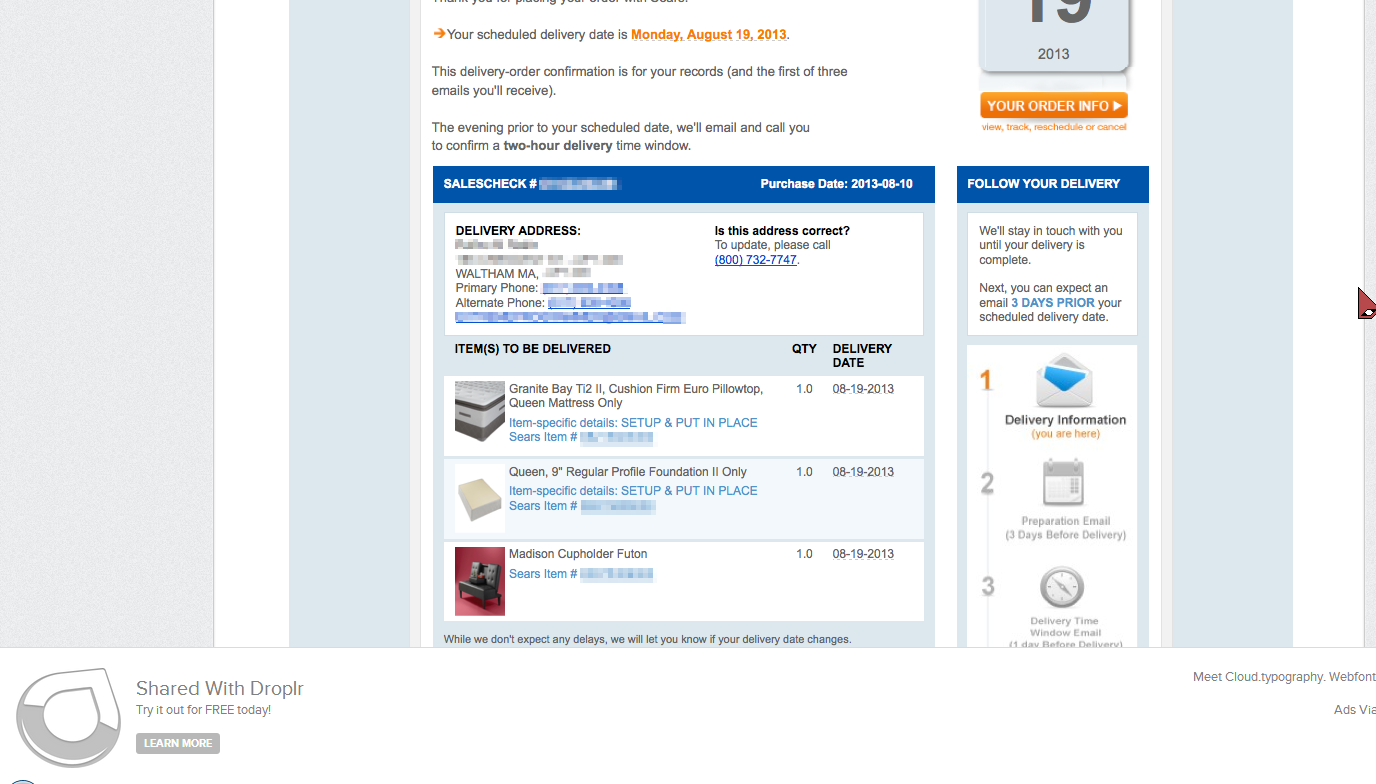
After only a little time manually appending random alphanumeric paths to
http://d.pr/, I came upon someone's order from Sears. Complete with
two phone numbers, address, order number, and email. Someone was upgrading their
sleeping experience, apparently –

[Code redacted] Note: While this code is trivial to write, I felt it prudent to remove it from the article. Seriously, it was 24 lines of Perl.Finally, it seems clear that Droplr understood these issues when they designed their service, or at least grokked them soon enough. A couple snippets from their Terms & Conditions:
Your Droplr.com Account and Site. If you create an account on the Website, you are responsible for maintaining the security of your account, and you are fully responsible for all activities that occur under the account and any other actions taken in connection with the account.
Responsibility of Website Visitors. ... The Website may also contain material that violates the privacy or publicity rights, or infringes the intellectual property and other proprietary rights, of third parties, or the downloading, copying or use of which is subject to additional terms and conditions, stated or unstated. Droplr disclaims any responsibility for any harm resulting from the use by visitors of the Website, or from any downloading by those visitors of content there posted.And so on. This is a pretty familiar attitude in the cloud. If you can achieve simplicity and convenience, everything else is negligible.